IPv6 Day 2016
Today is IPv6 day. IPv6 day aims to evaluate and promote public IPv6 deployment as it was designed to eventually completely replace IPv4. We embrace IPv6 technology at Dogsbody Technology and want to help promote it, so we thought we’d write a blog post telling you why we think it’s great. But first, what is […]
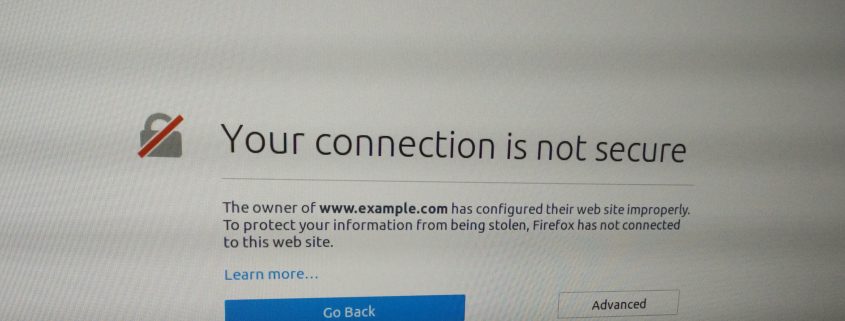
Certificate Authorities or how to trust over the internet
A common misconception we see all the time is that HTTPS is only useful for scrambling (encrypting) connections between you and a website, but this is only half of its potential. So how do we know we are connected to Facebook’s servers when we access www.facebook.com? HTTPS ensures this, by making two important aspects of […]
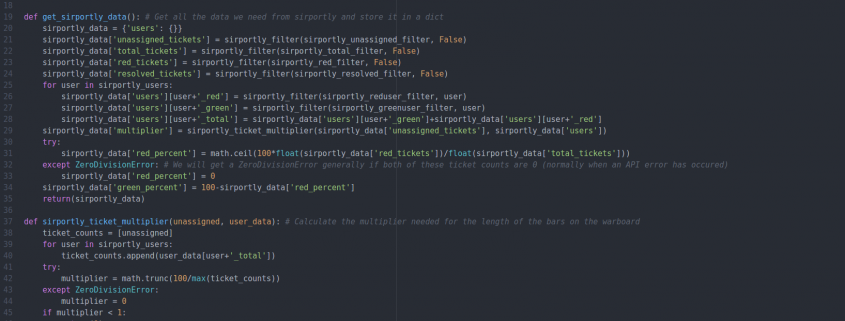
The Warboard
The Dogsbody Technology Warboard sits on the wall in our office and allows us to see a detailed overview of the infrastructure we monitor real time, this has proved it’s self to be invaluable for spotting potential issues and remedying them before they ever become an issue. We’re responsible for monitoring and maintaining hundreds of […]
What time is it? – About NTP
In this blog post we’ll talk about time, how it works, why it’s important to computers, and how NTP can be used to manage the time on computer systems. “You may delay, but time will not.” ― Benjamin Franklin Intro to NTP NTP (Network Time Protocol) allows computers on a network to synchronise their system […]
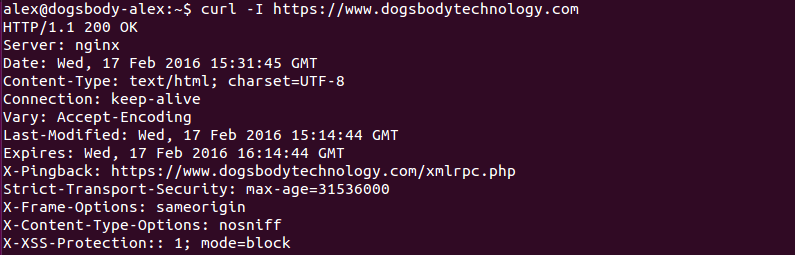
HTTPS Everywhere
“HTTPS Everywhere” is an increasingly popular trend among websites which gives added security, speed and SEO benefits. In August 2014, Google announced that it would be adjusting it’s search engine ranking algorithm to benefit HTTPS only sites, this was one of the key announcements that started the trend of sites going HTTPS everywhere. There’s also […]
The Dark Art of Email Deliverability
We often get questions over the technologies which help get your legitimate email delivered. There are three main ones: SPF – Used to lock down email sources to your servers DKIM – To authenticate your sent emails DMARC – For real world email reporting and DKIM enforcement Email is vital to any organisation. Ensuring your […]